Strengthening Your Cloud: Crucial Security Tactics for Safeguarding Your Assets
What does "strengthening your cloud" mean?
It means implementing security measures in the cloud computing environment to safeguard your digital assets, such as data, applications, and infrastructure, against unauthorized access, data breaches, and other cyber threats.
The popularity of cloud computing among businesses of all sizes is due to its scalability, flexibility, and cost-effectiveness. However, as more organizations transfer their data and applications to the cloud, the risk of cyberattacks and data breaches increases. To mitigate these risks, it is vital to strengthen the security of the cloud environment by implementing security strategies that safeguard resources from potential security threats.
Why Is Cloud Security Important?
As businesses increasingly move towards a completely digital environment, cloud computing has become a popular option. However, this also brings the added risk of cybersecurity challenges. Therefore, it is crucial to understand the importance of cloud security to ensure the safety of the organization.
Security threats have become more sophisticated over time, with new adversaries emerging each year. With remote access to all components available 24/7 in the cloud, a lack of cloud security can put all the collected data in danger simultaneously. Organizations that neglect to invest in cloud security may face significant problems, including potential data breaches and noncompliance when handling sensitive customer data.
Cloud security should be an essential component of any organization's cybersecurity strategy, regardless of its size. Many people believe that only large enterprises are targeted by cyberattacks, but small and medium-sized businesses are also prime targets for threat actors.
Essential security strategies to fortify the cloud and protect your resources:
Identity and Access Management (IAM): IAM is the process of managing user identities and controlling access to resources in the cloud environment. IAM helps to prevent unauthorized access to sensitive data and applications. With IAM, you can create policies that define who can access your resources and what actions they can perform. IAM also enables you to manage user access to resources, which allows you to limit access to specific users or groups.
Data Encryption: Data encryption is the process of encoding data to prevent unauthorized access. Encryption is a critical security measure that helps to protect sensitive data, such as financial information, personal information, and intellectual property. When data is encrypted, it's only accessible to authorized users who have the encryption key. Encryption ensures that even if an attacker gains access to the data, they won't be able to read or use it.
Network Security: Network security refers to securing the network infrastructure in the cloud environment. Network security measures include firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs). Firewalls help to prevent unauthorized access to the network by blocking unwanted traffic. Intrusion detection and prevention systems monitor network traffic for potential security threats and take action to prevent them. VPNs help to secure network traffic by encrypting data in transit.
Regular Security Assessments and Audits: Regular security assessments and audits help to identify potential security risks and vulnerabilities in the cloud environment. Security assessments and audits include penetration testing, vulnerability scanning, and security reviews. These assessments help to identify security weaknesses, and remediation plans can be put in place to address them.
Disaster Recovery and Business Continuity Planning: Disaster recovery and business continuity planning are critical components of cloud security. These measures help to ensure that your business can continue to operate in the event of a disaster or security breach. Disaster recovery plans include backup and recovery procedures, while business continuity plans include strategies for keeping your business running during a crisis.
By implementing these security strategies, you can ensure the confidentiality, integrity, and availability of your resources in the cloud and minimize the risk of cyber-attacks and data breaches.
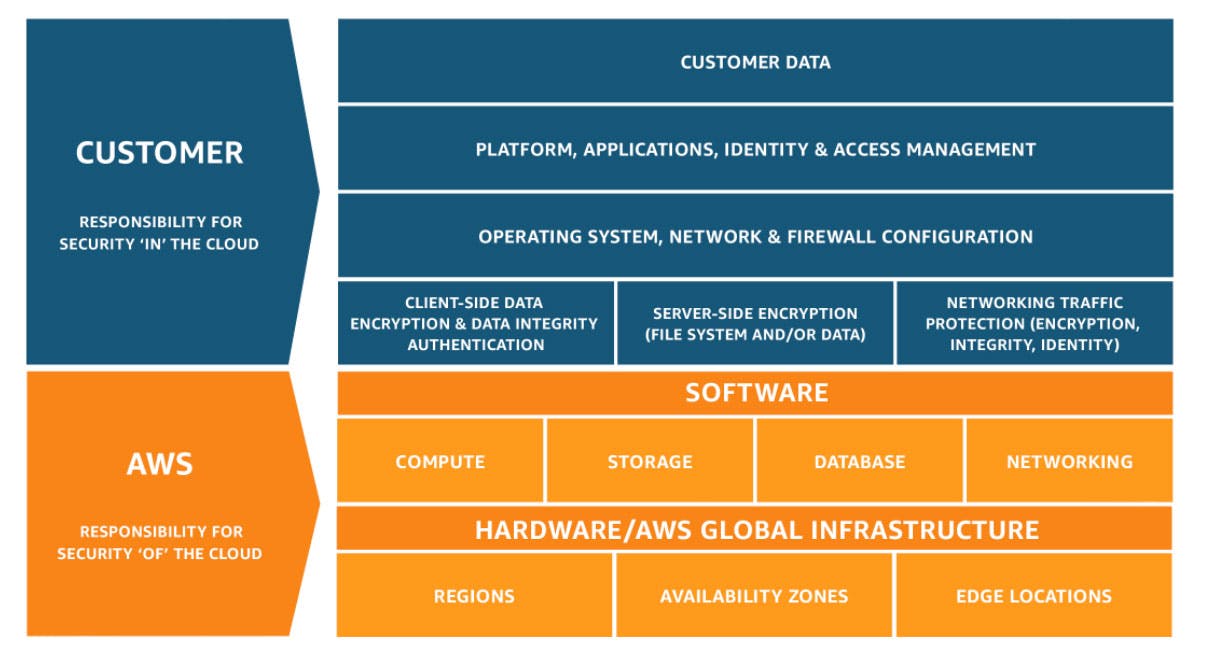
The shared responsibility model
Cloud service providers (CSPs) like GCP, AWS, and Azure host data and apps for most organizations. Cloud security is a shared responsibility between the CSPs and their customers, as outlined in the Shared Responsibility Model based on the type of cloud service.
Below is an example of the AWS Cloud Shared Responsibility Model:
Summary
Fortifying the cloud is critical to protect your resources, infrastructure, and business operations. Implementing these essential security strategies, including
IAM, data encryption, network security, regular security assessments and audits, anddisaster recovery and business continuity planningwill help to minimize the risk of cyber-attacks and data breaches. By taking the necessary security measures, you can ensure the confidentiality, integrity, and availability of your resources in the cloud.

