Introduction
Linux is an incredibly versatile operating system, used by millions of people around the world for everything from personal computing to enterprise-grade infrastructure. One of the key features of Linux is that it is divided into two distinct spaces: user space and kernel space. Understanding the difference between these two spaces is crucial if you want to work effectively with Linux, whether you are a developer, systems administrator, or just an enthusiastic user. In this article, we will explore the intricacies of user space and kernel space, discussing how they differ from each other, how they interact, and why it's important to maintain a clear separation between them. Join me as we delve deep into exploring the two worlds of Linux: User Space and Kernel Space.
User Space
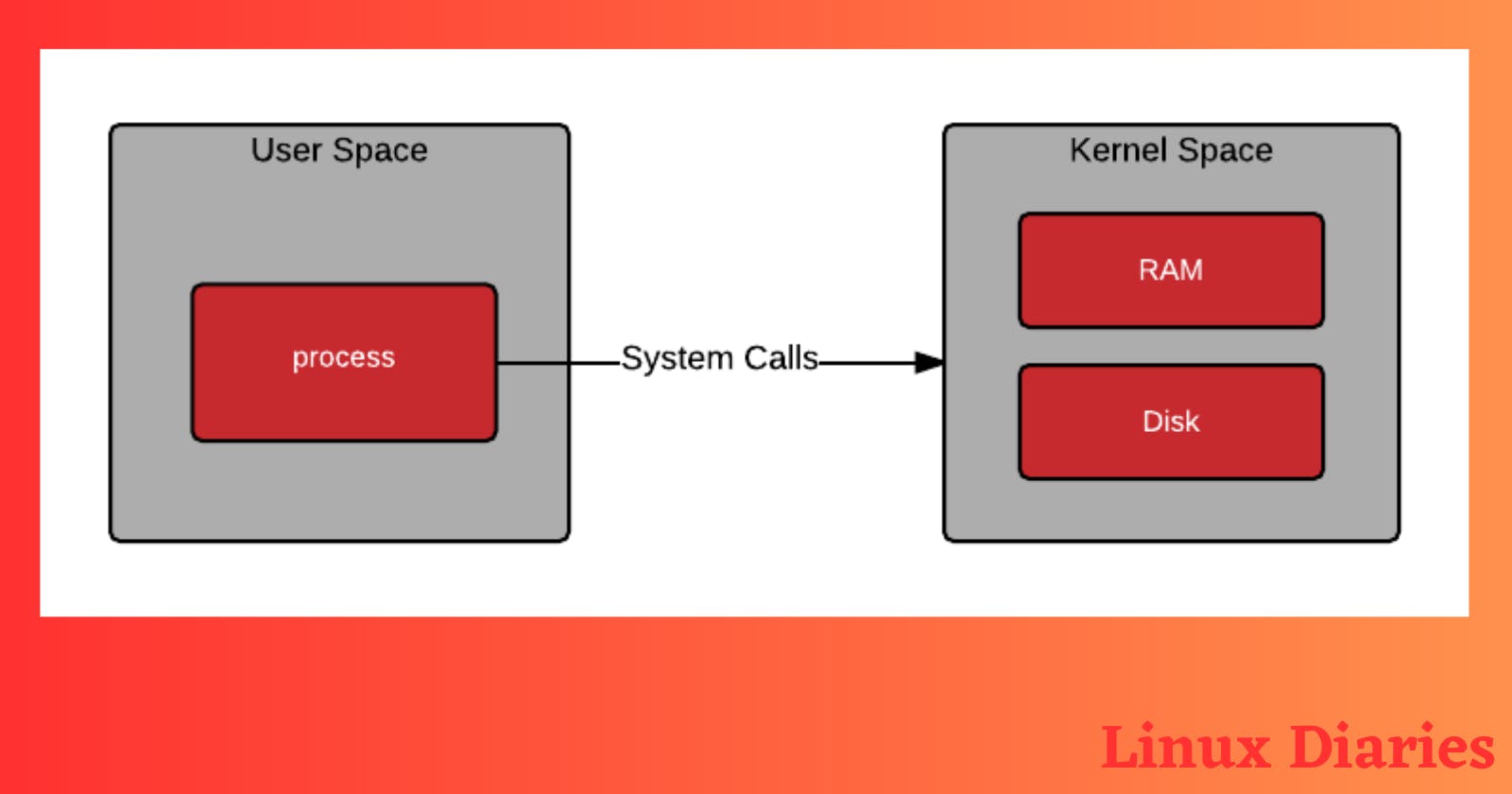
In Linux, user space is part of the operating system where user applications run. It includes all the applications a user interacts with, such as web browsers, text editors, and media players. This is different from the kernel space, which is where the operating system core and device drivers reside.
In user space, there are various layers such as the shell, system libraries, and user applications. The shell, also known as the command-line interface, is the gateway for users to interact with the operating system via text commands. System libraries are collections of precompiled code that are used by user applications to interact with the operating system. They provide standardized interfaces for tasks such as file input/output, networking, and process management. User applications are the programs that the user directly interacts with, such as web browsers, text editors, and gaming software.
Bottom-line, user space is where the majority of user interactions with Linux take place. It is where the applications that users use daily run, and it is crucial to have a clear understanding of how it works to maximize the efficiency and effectiveness of those interactions.
Kernel Space
In Linux, the kernel space is part of the operating system where the operating system core, also known as the kernel, and device drivers reside. It is used to interact directly with the hardware and manage system resources such as memory, CPU, and input/output devices. Unlike the user space which is where user applications run, the kernel space is protected and inaccessible to regular user applications.
The kernel space is divided into different layers such as the device drivers, file system, and system calls. The device drivers are responsible for interacting with the hardware devices such as the keyboard, mouse or network card. They provide the necessary interfaces for user applications to access these hardware devices. The file system, as the name suggests, is responsible for managing the files and directories on the system. It provides a common interface for user applications to perform file input/output operations such as reading and writing files.
Lastly, the system calls are the gateways for user applications to access the services provided by the kernel. System calls are low-level functions that allow user applications to interact with the kernel for tasks such as process management, memory allocation, and networking.
To sum up, the kernel space is an essential part of the Linux operating system where the core functionality, hardware interaction and resource management take place. It is divided into different layers such as device drivers, file system and system calls, which provide the necessary interfaces and services for user applications to execute on the system.
Interaction between User Space and Kernel Space
In an operating system such as Linux, user space and kernel space work together to execute programs and manage system resources efficiently. User space is where the user-level applications run, while kernel space is where the operating system code and device drivers interact with hardware and manage system resources.
The interaction between user space and kernel space happens through system calls, which are typically initiated by user-level applications. System calls are low-level programming interfaces through which applications can request services from the kernel space. For example, when an application needs to open a file, it will execute a system call to the kernel that will provide the necessary file access controls and operations.
Another way that user space and kernel space can interact is through interrupts. Interrupts are signals that the hardware devices send to the kernel when they need attention or have completed a task. For example, when a user presses a key on the keyboard, a hardware interrupt is generated, and the kernel retrieves the input.
The kernel space can also generate interrupts to signal the user space of certain events. For example, when a file is modified, the kernel can generate an interrupt to signal the user space of the changes.
Overall, the interaction between user space and kernel space in Linux is essential for the efficient execution of programs and management of system resources. System calls and interrupts are two mechanisms through which these two spaces interact with each other.

Differences between User Space and Kernel Space
User space and kernel space are two separate memory spaces that exist in an operating system such as Linux. They have several differences based on their respective functionalities, memory access, system resource usage, and process management.
Memory Access: User space is a protected memory space where user-level applications run. Applications can only access the memory space allocated to them, and they cannot access any restricted memory space or hardware directly. On the other hand, kernel space is an unrestricted memory space that contains the operating system code, device drivers, and other critical system resources. It can access any part of the memory space, including hardware.
System Resources Usage: User-level applications use system resources, such as CPU time, memory, and I/O operations, through system calls to the kernel. The kernel manages these resources and protects them from malicious or unauthorized access from user space. Conversely, the kernel space has unrestricted access to system resources and manages them directly.
Process Management: The user space manages user-level processes using the processes' virtual memory space by allocating and deallocating memory, scheduling CPU time, and handling signals. In contrast, the kernel space manages kernel-level processes, such as device drivers, system calls, and other critical system processes.
Protection: User space is typically protected from any crashes or malfunctions in the operating system as long as the applications are well-written and do not have any security vulnerabilities. Conversely, the kernel space is not protected from crashes or malfunctions and requires careful debugging to ensure the system's stability.
In short, user space and kernel space are two distinct memory spaces in an operating system. They have different functionalities, memory access, resource usage, and process management methods. The kernel space is responsible for managing system resources, whereas the user space is responsible for managing user-level applications.
Security
Maintaining security between user space and kernel space is essential as they have different levels of privileges and access rights. Kernel space has access to system resources and critical operating system code, making it vital to protect the kernel space from any unauthorized access or malicious attacks. At the same time, user space holds user-level applications, which must be protected from any malicious or unauthorized system-level access.
Any vulnerability in either space can lead to potential security threats that can impact the system's stability and the user's data. Some of the most common security vulnerabilities that can occur when working with each space include:
- User Space vulnerabilities
Buffer overflows: This occurs when an application tries to write more data to a buffer than it can handle, resulting in memory corruptions that an attacker can exploit to escalate privileges or execute malicious code.
Injection attacks: These vulnerabilities happen when an application doesn't validate user input accurately, allowing attackers to manipulate data and gain unauthorized access to the system.
Access control: This happens when applications improperly manage access control, allowing unauthorized users to access restricted resources.
- Kernel Space vulnerabilities
Rootkits: These are malicious software programs that are installed on a system and are designed to conceal their presence from anti-virus software and firewalls. Rootkits can hijack system calls to take over the system's security mechanism, allowing attackers to escalate privileges or execute malicious code.
Device Driver vulnerabilities: Device drivers are a critical component of the operating system, and any security vulnerability in a device driver can lead to system compromise.
Semantic vulnerabilities: This happens when the system calls with different function parameters lead to kernel-level memory corruption or buffer overflow.
In conclusion, maintaining security between user space and kernel space is essential in securing the system from potential attacks. To mitigate these vulnerabilities, developers and system administrators must be vigilant in identifying and patching any vulnerabilities that arise in either space. Additionally, implementing proper access and control policies and using secure coding practices can help minimize these security risks.

How do you explain user space and kernel space in linux in layman's terms?
In Linux, there are two different playgrounds where different things happen. One playground is for grown-ups, and the other is a special playground for kids. The grown-up playground is called the kernel space, and it has all the important tools to manage the computer, like controlling the lights, fans, and sounds. The kids' playground is called the user space, and it has toys, games, and fun things to play with, like puzzles, music, and videos. The grown-up playground is fenced off from the kids' playground to keep the grown-up things safe and secure. Just like how parents like to protect their tools and gadgets so their little ones don't break them, the kernel space is protected from the user space so that the computer doesn't break.
Conclusion
In conclusion, understanding the concept of user space and kernel space is essential to Linux users. The article highlights the fundamental differences between user space and kernel space and why it's crucial to maintain security between them.
The user space is where user-level applications run, while the kernel space manages essential operating system components, including system resources and hardware. Communication between the two spaces occurs through system calls, which are used to request services from the kernel.
Understanding this concept is crucial in Linux systems administration, especially when troubleshooting issues. It helps identify the source of system crashes or performance issues and how to mitigate them.
Additionally, understanding user space and kernel space security risks is crucial for developers and system administrators. Common vulnerabilities such as buffer overflows, injection attacks, and device driver issues can compromise the system, leading to data loss, system crashes or even complete control takeover by hackers.
In conclusion, a fundamental understanding of user space and kernel space in Linux systems enhances system performance and security while minimizing the risk of potential attacks on the system.